
By Eliot Rabaud
Sun Dec 24 2023
05
05
What is Ethical hacking (Pentest)?
Deciphering
Ethical hacking, also known as intrusion audit, penetration testing or pentesting, consists in evaluating the security of a computer system or network using the techniques and tools of hackers, but in a legal and controlled way. An intrusion audit (pentest) is a mandatory phase when you want to secure yours or your client’s data. Whether the pentest is conducted on internal, external, cloud infrastructure, or a web application, the goal remains the same: Simulate attacks to assess and improve the security of an informatic system. This proactive approach is crucial for identifying and correcting vulnerabilities before they are maliciously exploited.
Pentesters adopt the perspective of an attacker, using similar approaches and tools. Consequently, the results of an audit reflects what a potential attacker might discover and exploit.
Unlike the services of a “Blue team” or consulting, which focus on setting up technical and organizational defenses to minimize a successful attack (such as firewall rules, monitoring, an application firewall (WAF), etc.), a pentest takes a more direct and technical approach. Recommendations from a pentest aim to eliminate attack vectors upstream of exploitation by correcting vulnerabilities, through means such as modifying the source code, updating systems, or removing problematic configurations.
Different Approaches to Pentesting
The diversity of penetration testing approaches - black box, gray box, and white box - offers varied but complementary perspectives on system security. Each method brings a different depth of analysis, ranging from total ignorance of the system (black box) to complete knowledge (white box), with an intermediate level of knowledge (gray box). However, regardless of the chosen approach, the objective remains constant: to detect weaknesses and strengthen security.
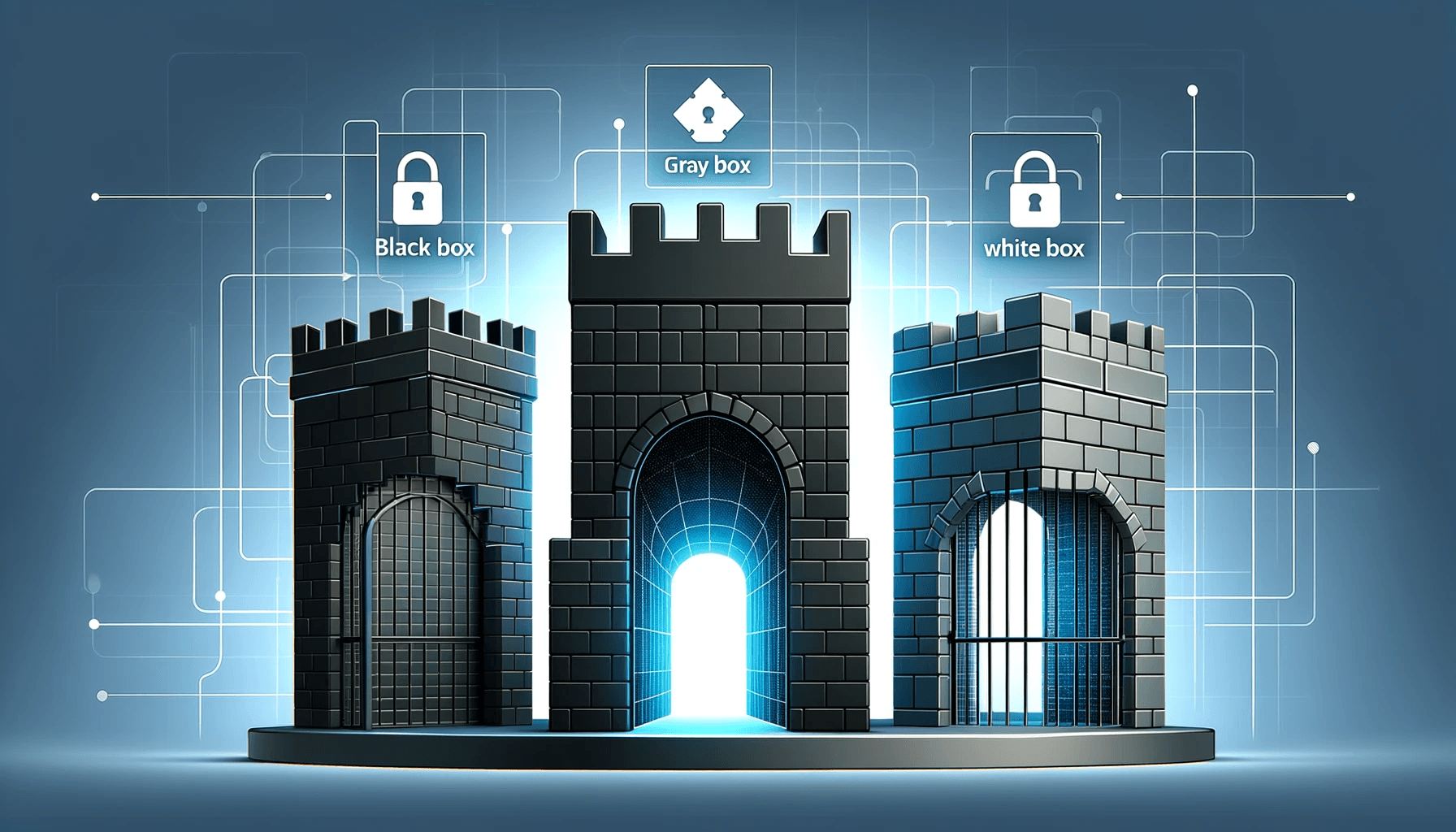
Black Box
In a black box type pentest, the tester has no prior knowledge of the targeted system. This approach emulates an external attacker attempting to penetrate the system without internal information. A black box audit can be the ideal approach for a company that has never conducted an audit and wants a first assessment of their external defenses.
Gray Box
The gray box type pentest lies between black box and white box approaches. Here, the pentester has some information about the internal infrastructure, such as credentials, database schemas, but not the source code, for example. This method offers a balance between external exploration and internal knowledge. A gray box pentest is perfect for SAAS applications or a company’s internal infrastructure.
White Box
In a white box approach, the tester has complete access to system data, including architectural diagrams, source code, and credentials. This method allows for a deep analysis of security. The white box approach can be interesting for companies that have already conducted a pentest or are confident in their defenses. This type of audit allows for the detection of problems that are difficult to find or test without these informations. It also helps to bridge the time deficit a pentester might have compared to an attacker. With access to all this information, the pentester can move much faster in their analysis and therefore spend more time on exploitation and chaining vulnerabilities to increase the impact of the found issues.
Pentest Methodology:
To ensure the quality and effectiveness of a penetration test, it is important to follow a strict methodology. Several organizations have created guides and methodologies to standardize penetration tests. Although the intrinsic quality of the pentester will of course be decisive in the final results. The use of these guides limits the quality gap between different pentests.
At DungeonData, we follow the steps of the OWASP “testing guide” and use the “Common Vulnerability Scoring System (CVSS)” method to standardize the rating of the vulnerabilities, thus allowing effective prioritization of fixes.
The OWASP Testing Guide is primarily oriented towards web application pentests, but the different steps of the penetration test are extracted from the “Penetration Testing Execution Standard” (PTES) and can apply to all types of penetration tests. These steps guide the pentest from start to finish, both technically and organizationally.
The steps include:
- Pre-engagement Interactions
- Intelligence Gathering
- Threat Modeling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Reporting
For more information on the CVSS and the OWASP Testing Guide, you can consult the following links:
- CVSS: https://fr.wikipedia.org/wiki/Common_Vulnerability_Scoring_System
- PTES: http://www.pentest-standard.org/index.php/PTES_Technical_Guidelines
- OWASP testing guide: https://owasp.org/www-project-web-security-testing-guide/
Pentest is not an option
By simulating attacks, pentesters provide an essential perspective that helps build up an IT system’s defenses against real threats.
In a world where digital threats are constantly evolving, Pentests prove to be more than just a precautionary measure – they are a necessity. By regularly integrating pentests into security practices, organizations can anticipate and protect against attacks, thus ensuring the security of their data and the trust of their users.